Maybe the source of the problem is not where there is the most noise…
I’ve got an idea percolating but I’m not sure how to model it yet. Apologies up front for not being super-specific, if I can reason out enough pieces of this idea I will hopefully harness it for a paper I’m planning to write later this year.
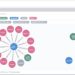
Some types of attacks have so much human behavior in them that there is no system rule you can put in place to detect. I was watching some videos from the Association of Certified Fraud Examiners (ACFE) and I stopped on Kathy Lavinder’s “Power of Weak Connections” on YouTube. She says that it is not always your strong, personal connections in your professional network that help you get news jobs – it is the weak connections with people who know you just enough to help move a resume or an inquiry into the right hands.
There is energy and opportunity in the kinetic connections between two sources. But what if the crux of the opportunity is in the weak connection rather than the strong connection? Does this idea carry into the cyber attacks and fraud detection?
Visualize
I’d like to analyze that data, and see the strengths of the connections. Does the hypothesis of the weak connection providing a strong vector hold up under the math? I’m reading about UML and graph databases to look for a way to re-categorize some existing data in order to redraw and reexamine the connections. It seems soft to compare a fraud or cyber attack to a business process modeling method, although I am certain I will learn something and I’m looking forward to applying some old techniques in a slightly different way.