A Microsoft Technet article by John Lambert from 2 years ago includes this quote, and I’ve seen it used many times since then:
“Defenders think in lists. Attackers think in graphs.”
To me, this statement means that there are multiple possible paths available to get to an end if you can pivot and reorient while working through an environment. The environment may have been designed in a systematic hierarchy to maximize organization efficiency, but that doesn’t mean a wily actor can’t create their own circuitous route.
I mentioned in a previous post that I’ve been learning to dabble in Graph Databases. In fact, I am working to build a graph representation of the connections and pivots available in the logs and data typically available to an analyst in an investigation (inspired by one of my favorite parts of the Investigation Theory course).
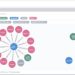
Unlike a relational database, a graph database uses nodes, edges, and properties to build and describe relationships. Wikipedia describes the graph theory behind a graph database better than I can, but I put together the visualization below before my free trial of MindJet MindManager expired. If you can determine your nodes, labels, properties, and relationships – you can connect and visualize the net of assets and relationships in your scope. Let’s use the sample graph visualization of two colleagues names Bob and Cathy.
- Nodes contain properties and are tagged with labels.
- The person is a node, the property is their name and the labels are their position and their prestige.
- Relationships connect nodes, have direction, and contain properties.
- The relationships describe how the nodes (persons) are working and hiring.
I’ve been learning Neo4j to build a graph database. Download this free Graph Databases ebook from O’Reilly to get started. I’ve also watched some videos in an Intro to Neo4j course hosted by Lynda (which normally has a cost but can be accessed with my library card for free via the elearning offerings on my local library’s website). I’d also like to buy Learning Neo4j Graphs and Cypher book and video from Packt Publisher in the future.
In the starter use case I’m building out in my own Neo4j instance, the nodes are both data sources and data elements, and the relationships describe where the data elements are contained. The idea behind this is that if an analyst had one piece of data and wanted to get to another piece of data, they could explore the graph to see which nodes they have available to traverse in order to pivot the data from what you have to what you want.
For instance, if you have the IDS Alert available providing you a signature and protocol, but you need to know the details of the certificate used in the transaction, you can pivot fro the IDS alert through the PCAP and SSL Transaction to get to your destination.
I am still experimenting, I know my test data is imperfect. Ideally, you could research the sources and elements available within your enterprise to create your Cypher code and output a visual database that allows you to look or query for a solution path. Somehow it feels much more impressive when you look at the connections for the data elements of a dozen or so different data sources at once.
This is a solid idea for a learning opportunity and a rough first implementation try. I’ll think on it some more and work to eventually hone something useful and repeatable that doesn’t take much effort to keep up to date. If you have any input, feel free to use the contact form on my website and reach out.